

Do you know that Cybersecurity professionals are in high demand with over 500,000 open cybersecurity positions across the U.S. and more than two million worldwide? Cybersecurity talent gaps exist across the country. Closing these gaps requires detailed knowledge of the cybersecurity workforce. There are many opportunities for workers to start and advance their careers within cybersecurity.
According to the U.S. Bureau of Labor Statistics, the job market for information security analysts will grow by 32 percent by 2028 -- making it one of the fastest growing job sectors -- while Cybersecurity Ventures has found that there will be 3.5 million unfilled cybersecurity jobs in 2021. This means that cybersecurity professionals are among the most in-demand around the world and will be for years to come.
Becoming a well-rounded cybersecurity professional requires having well-rounded experience. Exposure and experience are critical building blocks of a cybersecurity career early on and will also become valuable (and make you more effective) as your career progresses and you become a senior cybersecurity leader. More importantly, exposure and experience allows you to learn which domains in cybersecurity you want to work in and you can then focus your career path more on those. Before committing to a domain of cybersecurity as a career path, it’s important to get exposure to different areas.
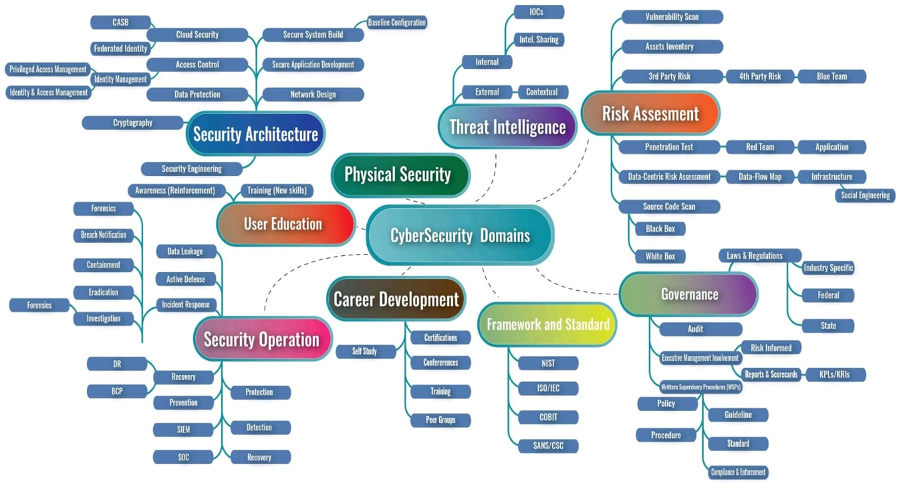
Cybersecurity personnel help organizations across industries bolster their security stance and prevent or thwart cyberattacks. This is especially important in today’s digitalized corporate world, where one data breach could lead to a company losing its credibility and goodwill, possibly forever.
Roles in the cybersecurity domain come with a wide variety of job titles and responsibilities, depending on numerous factors. For instance, different industries (such as finance and healthcare) will have different cybersecurity requirements, depending on regulatory and legal responsibilities. But at its core, cybersecurity is only about one thing — preventing sensitive data from falling into the wrong hands.
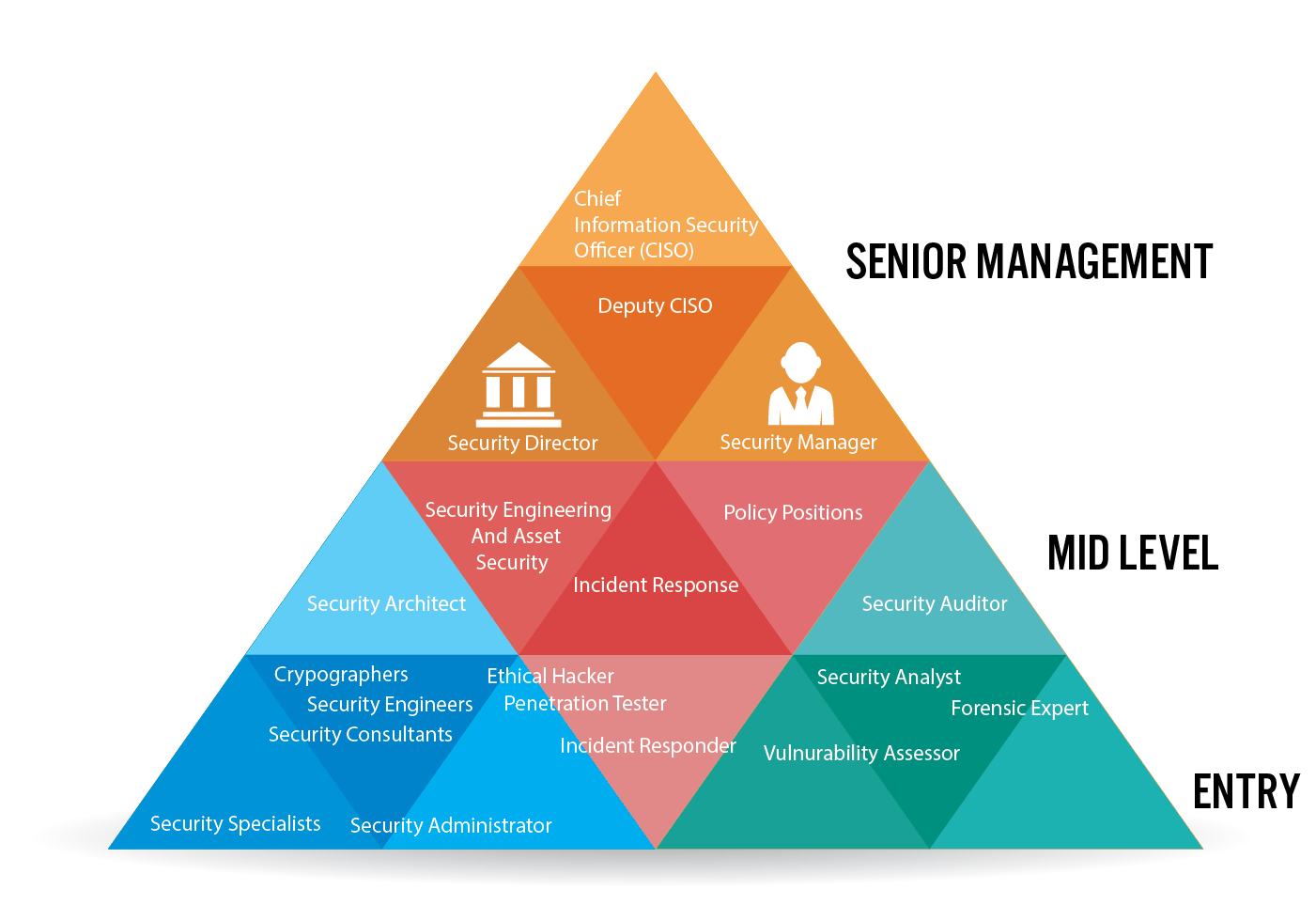
The Roles and job titles in the security sector often leads to overlapping of several responsibilities and are customized according to the size and needs of the organization. Different job roles like security analyst, security administration, security engineer, security architect and other consultant specialist are the typical job titles. As the cybersecurity domain keeps on expanding and developing all over the place further, new roles and titles are likely to emerge and the roles attributed to the current titles will likely crystallize or evolve.
Chief information officers are the highest position within a company that focuses on the information within a company or organization's systems. The chief of information provides guidance and leadership to specialists and managers within their department by creating regulations for security procedures. The chief information officer also considers data and aligns the company's technical strategy with its overall goals.
The director of security leads both information technology staff and managers of security. The director of security role for cybersecurity is often present in larger companies that dedicate bigger teams of professionals to maintaining systems security. The director provides leadership and guidance, creates and implements regulations and communicates with company executives about security situations.
A security manager is a leader who oversees security measures within an organization. Security managers with a focus on cybersecurity manage IT teams and develop strategies for cybersecurity efforts. They may also write rules and regulations regarding cybersecurity decisions.
Security specialists are the people who are responsible for their organization’s security. They check the systems and the connections for any security vulnerability. The onset of cloud trend has boosted this role as a security specialist is required to assess the cloud systems regularly.
An information security analyst gathers and assesses data to learn more about an organization's security profile. They can also collaborate with other security and information technology professionals to implement security measures and assess their performance. For example, an information security analyst may help implement a firewall within the system to protect important information.
Incident responders are people who not only detect the threats but also respond to them. These people help the organization and its employees to stay prepared and act when the security is breached.
Security administrators are the most essential personnel. Their tasks include roles of multiple titles. They set up proper security guidelines for the flow of data and also are responsible for installing firewalls and malware blockers.
Vulnerability assessor or vulnerable assessment analyst are people who run multiple tests on the systems. Their main aim is to find the critical flaws in the security system while also prioritizing things that affect the organization the most.
Cryptographers are the people who use cryptography techniques to encrypt and decrypt the data keeping it hidden from irrelevant parties. They are very essential and are more in demand.
Security managers supervise the rest of the team. They take important decisions and oversee the whole team’s work.
As the name suggests security architect are people who design the security structure. They also test out the security and respond to threats.
Security analysts analyze the systems and patch the loop holes. They often work together with the rest of the team of IT specialist and developers.
Security auditor are the people who are tasked with finding the breach in the system first before anyone else does. They check whether the currently installed firewalls and other security measures are working properly or not.
Forensic expert are people who trace back the hacks and breaches. They investigate cyberattacks or any other illegal activity taking place online. They try to revive any damaged or encrypted data related to the crime.
Penetration testers are people who are allowed to hack the system and try to find a way in. They act like hackers trying to attack the security system.
Security consultants are highly knowledgeable security professionals who help organizations identify ways in which they can improve their security measures. The security consultant can examine the current security system and help leaders understand where they don't function well and how to improve them. Consultants may suggest specific security systems or products depending on the organization's needs.
Security engineers patch, maintain and remove stuffs on the system. They work directly on the system and are responsible for the modification of the system.
A network security engineer focuses on how devices and computers connect to one another using the internet. Network security engineers help implement security measures that apply to connections to the network and how a computer protects its information over the internet. Many cyberattacks can occur through the network an organization uses, so it's important that the network security engineer monitors potential breaches and implements strategies for protecting access and information within the business.
Crafting a career path in cybersecurity can be an exciting journey. There is no right or wrong answer. There is no strict path to success. It’s important to gain exposure to what’s available, try new things, learn as much as you can, and figure out what domains you love the most. Then consider whether you prefer to build more in-depth career paths within those domains or gain broad exposure in pursuit of more senior leadership roles. Considering career path options also doesn’t have to mean sticking to one domain. No matter which path is chosen, have fun learning and growing throughout the journey.
Cybersecurity Supply/Demand Heat Map (https://www.cyberseek.org/heatmap.html)
Cybersecurity Career Pathway (https://www.cyberseek.org/pathway.html)
Career Pathway Roadmap (https://niccs.cisa.gov/workforce-development/career-pathway-roadmap)
Cyber Career Pathways Tool (https://niccs.cisa.gov/workforce-development/cyber-career-pathways-tool)
Copyright © 2025 Trutekacademy, All rights reserved
Write a public review